You’ve worked carefully on your email marketing strategy but still face the problem of your emails bouncing or ending up in the spam folder all the time?
This is something no sales reps or marketers want to face. After all, bounces and a high spam complaint rate can be detrimental to one’s sender reputation, email deliverability, and can even lead to the sender getting blocked by ISPs.
But don’t worry. Been there, fixed that.
One of the reasons your emails may be marked as spam is the incorrect configuration of DMARC, DKIM, and SPF records.
To solve the problem, you need to know a few technical details. And that’s what we are here for!
Outline:
What do SPF, DKIM, and DMARC stand for?
Let’s start off with clearing up some terms.
When reading SPF, DKIM, and DMARC definitions, you will notice DNS being mentioned a lot. DNS (Domain Name System) is a repository of domain names (example.com) and their corresponding IP addresses (111.222.333.444). Each domain can have more than one IP address, for example, a subdomain or domain mail server will have different IPs.
To set up SPF, DKIM, and DMARC, you need access to DNS. Usually, your company’s system administrators or, in some cases, developers can help you with it.
SPF helps prevent spoofing by verifying the sender’s IP address
SPF (Sender Policy Framework) is a DNS record containing information about servers allowed to send emails from a specific domain (for example, snov.io).
With it, you can verify that messages coming from your domain are sent by mail servers and IP addresses authorized by you. This might be your email servers or servers of another company you use for your email sending.
If SPF isn’t set, scammers can take advantage of it and send fake messages that look like they come from you.
It’s important to remember that there can be only one SPF record for one domain. Within one SPF record, however, there can be several servers and IP addresses mentioned (for instance, if emails are sent from several mailing platforms).
DKIM shows that the email belongs to a specific organization
DKIM (DomainKeys Identified Mail) is another technical standard that helps identify fake email addresses, fight against spam, and prevent spoofing and identity theft.
DKIM adds a digital signature to the header of your email message, which email servers then check to ensure that the email content hasn’t changed. Like SPF, a DKIM record exists in the DNS.
DMARC aligns SPF and DKIM mechanisms
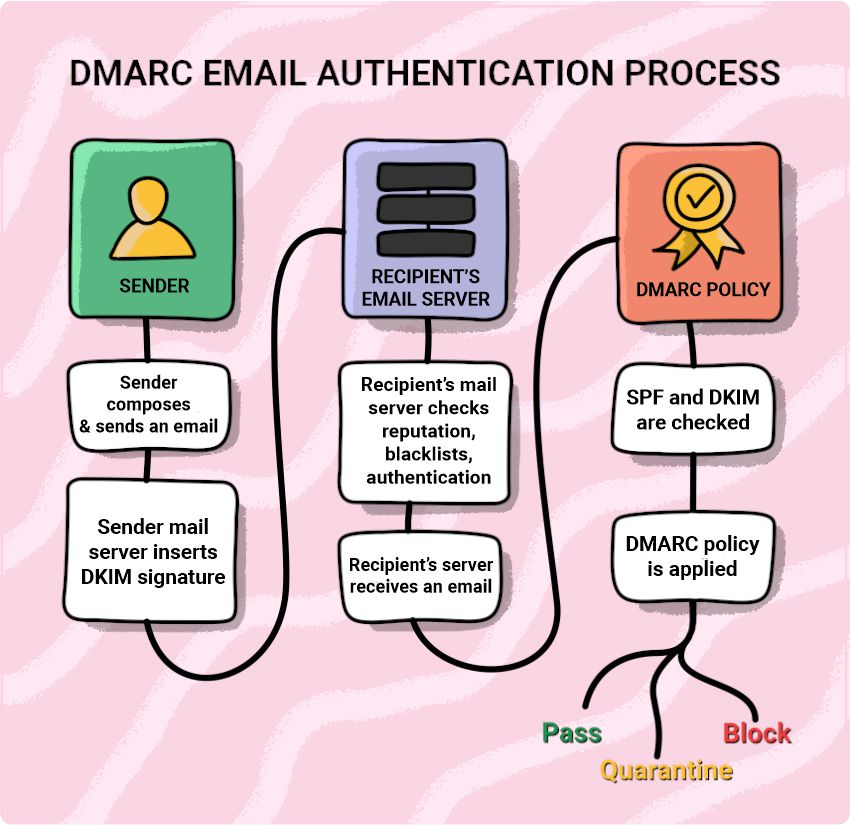
DMARC (Domain-based Message Authentication, Reporting & Conformance) defines how the recipient’s mail server should process incoming emails if they don’t pass the authentication check (either SPF, DKIM, or both).
Basically, if there’s a DKIM signature, and the sending server is found in the SPF records, the email is sent to the recipient’s inbox.
If the message fails authentication, it’s processed according to the selected DMARC policy: none, reject, or quarantine.
- Under the “none” policy, the receiving server doesn’t take any action if your emails fail authentication. It doesn’t impact your deliverability. But it also doesn’t protect you from scammers, so we don’t recommend setting it. Only by introducing stricter policies can you block them in the very beginning and let the world know you care about your customers and brand.
- Here, messages that come from your domain but don’t pass the DMARC check go to “quarantine.” In such a case, the provider is advised to send your email to the spam folder.
- Under the “reject” policy, the receiving server rejects all messages that don’t pass email authentication. This means such emails won’t reach an addressee and will result in a bounce.
The “reject” option is the most effective, but it’s better to choose it only if you are sure that everything is configured correctly.
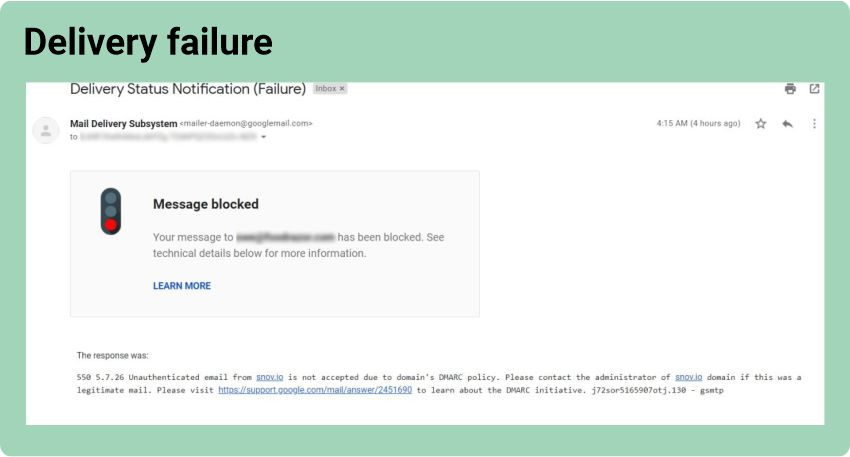
Now that we’ve clarified all the terms, let’s see how you can check if you have an existing SPF record, DKIM record, and DMARC policy set in place.

13 Best Email Warm-Up Tools (Tested And Compared)
19 September 2023
How can you check if your technical setup is okay?
Here are some easy ways to check your technical setup to see if everything is working correctly on its own.
DKIM, SPF, and DMARC check via Gmail
Option 1
Send a test email to your address and then open the message. Click “Show details.” If you see a “mailed-by” header with the domain name and a “signed-by” header with the sending domain, your DKIM and SPF are fine.
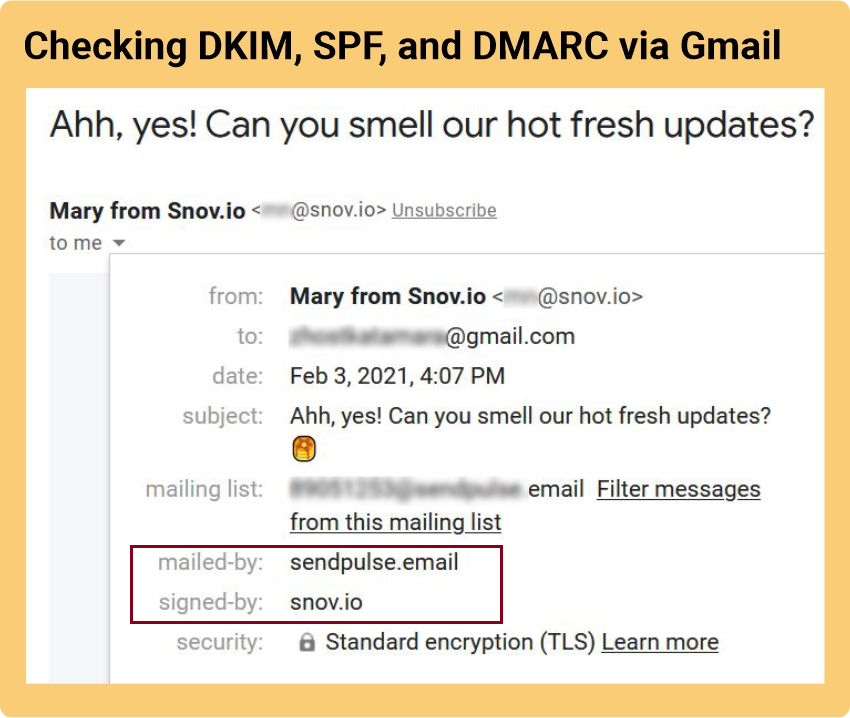
Option 2
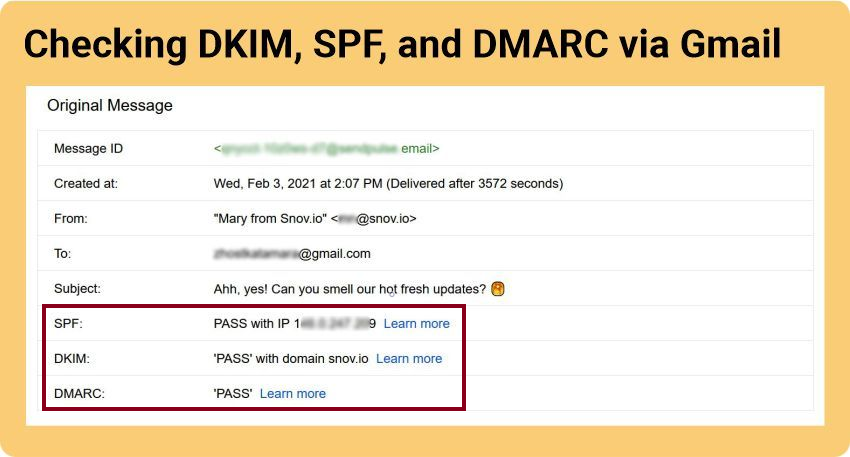
If you go to “Show original,” you can see more information on SPF, DKIM, and DMARC.
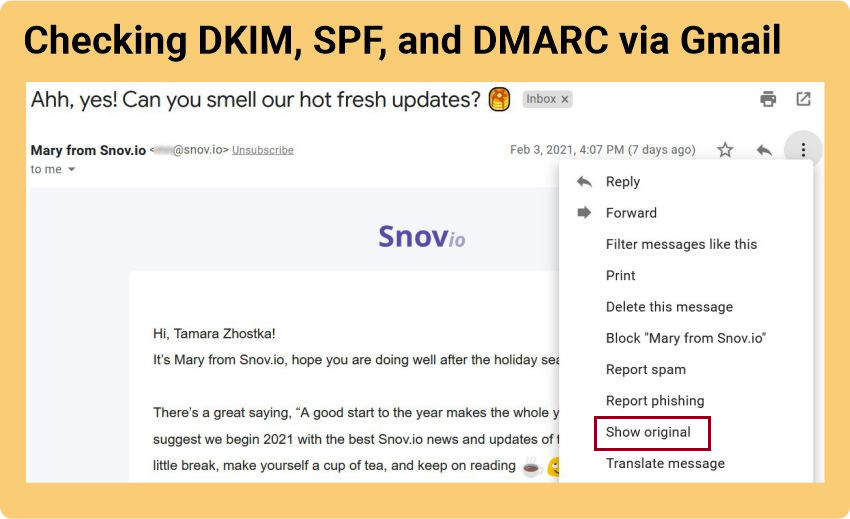
Done!
DKIM, SPF, and DMARC check via command line
Now let’s look at how you can check SPF, DKIM, and DMARC records in Windows through the command line. For Mac users, the process is a bit different; verification is done through the Mac OS Terminal. You can read the details here.
SPF record check
You can check your SPF record using nslookup — a default query tool that provides the user with a command-line interface to access the DNS.
- Open the command line (Start > Run > cmd).
- Enter “nslookup -type=txt” followed by a space and a domain or hostname, for example, “nslookup -type=txt google.com”.
- If an SPF record exists, the result will be something like this: “v=spf1 include:_spf.google.com ~all”.
- If there are no results or no “v=spf1”, then there is a problem getting the record for the domain, or it doesn’t exist.
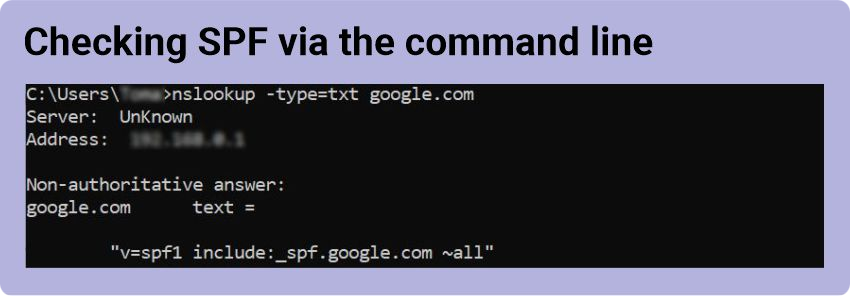
How to read SPF correctly
- The “v=spf1” part shows that the record is of SPF type (version 1).
- The “include” part lists servers allowed to send emails for the domain.
- The “~all” part indicates that if any part of the sent message doesn’t match the record, the recipient server will likely decline it.
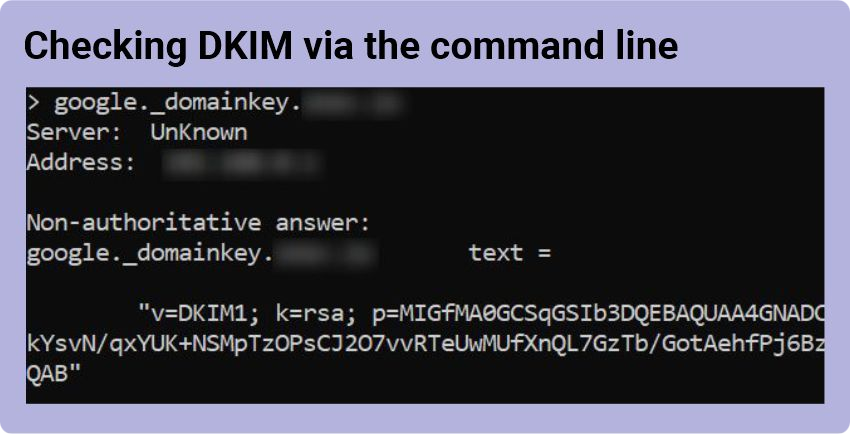
DKIM record check
To check DKIM with the help of nslookup, follow these steps:
- Open the command line (Start > Run > cmd).
- In the command window, type “nslookup” > Enter.
- Type “set q=txt” > Enter.
- Type “selector._domainkey.domain.com” > Enter. Substitute the words selector and domain with the DKIM selector and domain you want to look up.
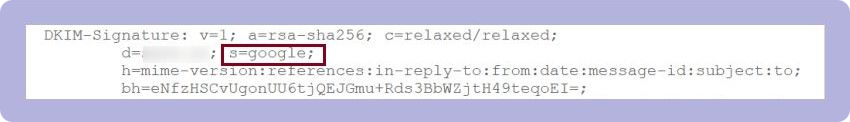
The DKIM selector can be found in the DKIM-Signature email header if you go to any email you’ve sent, click “Show Original” (like we did here), and scroll down. It’s specified as the “s=” tag.
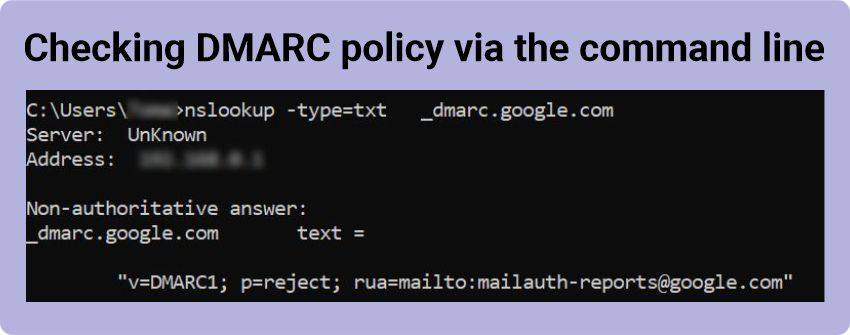
DMARC policy check
You can look up DMARC policy from the command line too:
- Open the command line (Start > Run > cmd).
- Type “nslookup -type=txt _dmarc.domain.com”, for example, “nslookup -type=txt _dmarc.google.com”, > Enter.
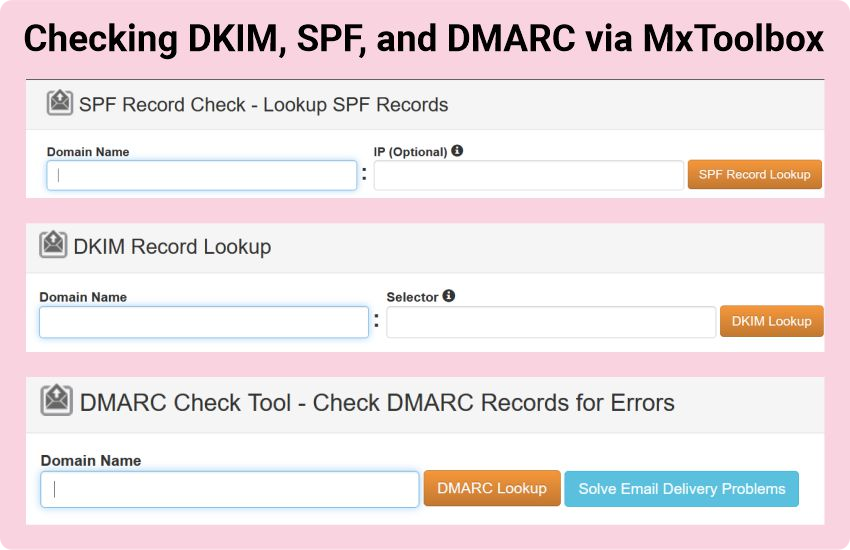
DKIM, SPF, and DMARC check with the help of MxToolbox
This one is, perhaps, the easiest option. All you need to do is go to the MxToolbox website and run three checks.
Please note that for the DKIM record lookup, you will need a selector, just like in the case with the command line we’ve described earlier.
How to set up SPF, DKIM, and DMARC?
While configuring SPF, DKIM, and DMARC records, you need to follow the correct order, which can be found in Google Workspace Admin Help.
These are the instructions you can follow:
- Set up SPF for the domain.
- Set up DKIM for the domain.
- Set up a mailbox for reports.
- Get the domain host sign-in information.
- Check for an existing DMARC record (you can use MxToolbox here).
- Change DMARC policy.
Remember that both the initial setting of DKIM, SPF, MX, DMARC and subsequent changes must be in the correct order.
Below you can find general settings for all domain providers (using Google as an example). But remember, since you have your own domains, they can all be configured differently.
General SPF setup
1. You need to go to your DNS settings (e.g., Namecheap, Cloudflare, Bluehost, etc.) and create a new record.
2. Select TXT record and enter “@” in “Name.”
3. Paste “v=spf1 include: _spf.google.com ~all” in “Value” and then save.

General DKIM setup
These steps are for the administrators who manage Google Accounts for your company:
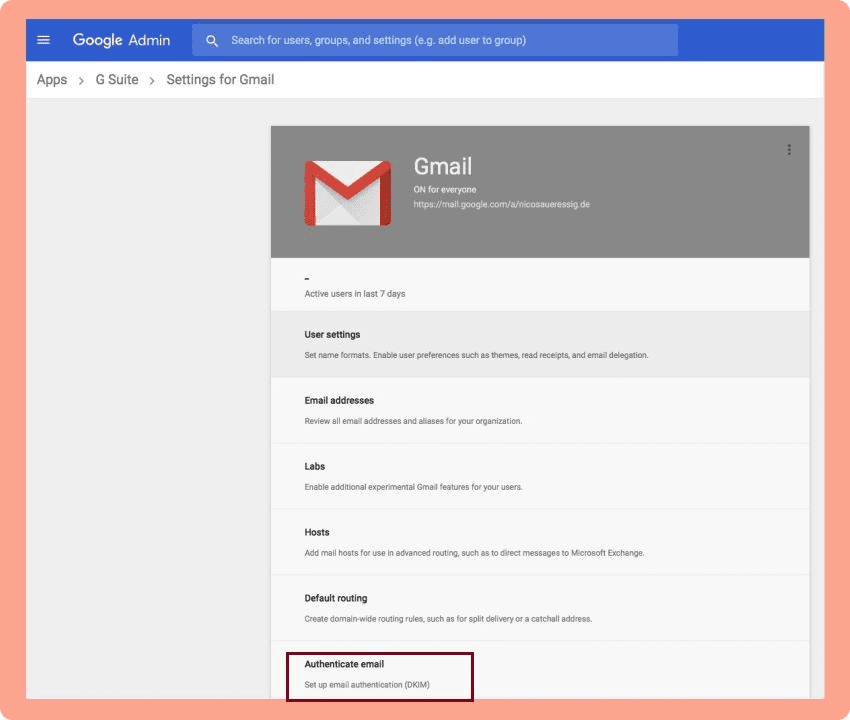
1. Sign in to your Google Admin console.
2. Click on the top left menu and head to Apps > G Suite > Settings for Gmail > Authenticate Email.
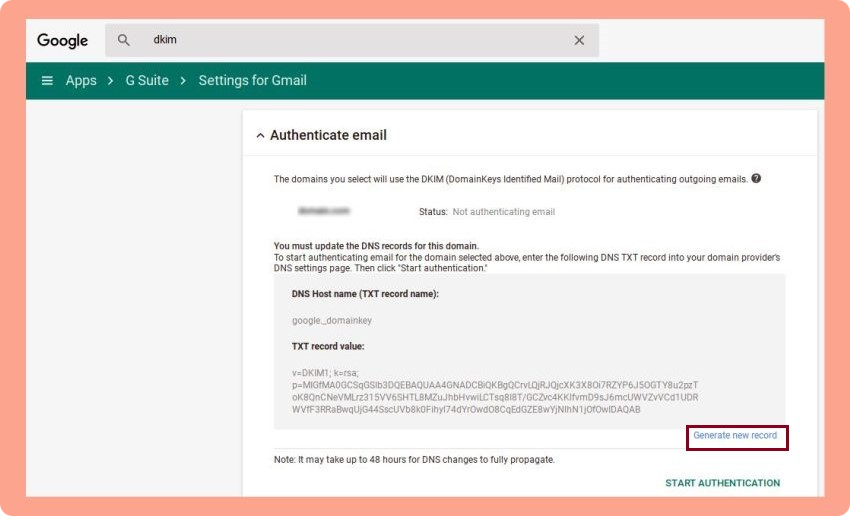
3. Pick your domain from the drop-down list, click “Generate New Record,” and then copy the hostname and the TXT record value.
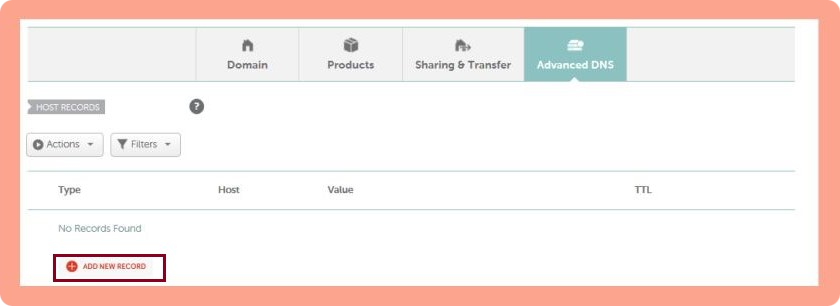
4. Log in to your DNS (e.g., Namecheap, Cloudflare, Bluehost, etc.), go to the domain list, choose your domain, and pick “Add New Record” in the advanced settings.

5. Select TXT record and enter the hostname you’ve just copied from Google in “Name” and TXT record value in “Value.”
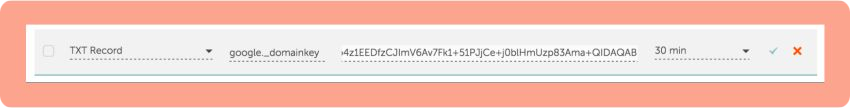 6. Save your changes.
6. Save your changes.
7. Go back to Google and simply click “Start Authentication.”
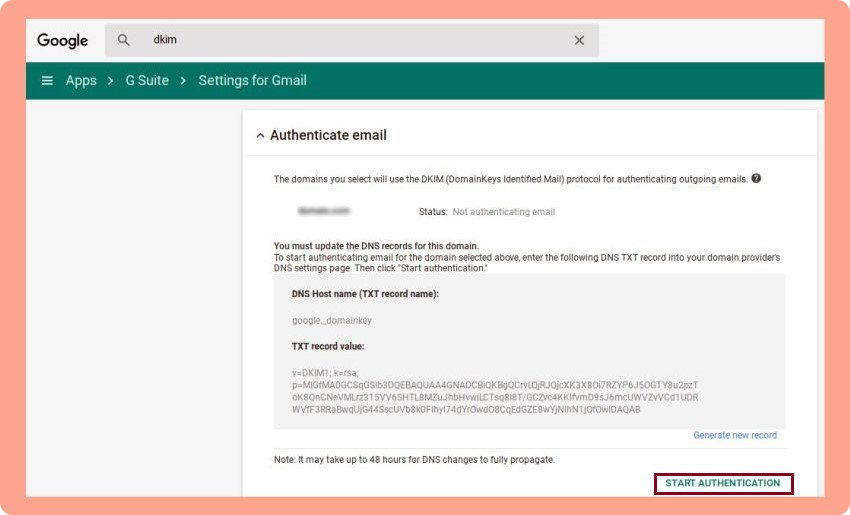
8. Wait for the DNS to update 🙂
Here’s a video instruction if you want a more detailed explanation:
General DMARC setting
Just like SPF and DKIM, DMARC is a simple one-line entry in your DNS records (e.g., Namecheap, Cloudflare, Bluehost, etc.).
Before setting it, make sure you’ve configured SPF and DKIM records for the required domain.
Then follow these steps:
1. Go to your DNS settings and create a new record.

2. Choose a ‘TXT’ record.
3. Add the hostname (for example, _dmarc).
4. Add the value. You can find a sample DMARC entry that you can use to create your own below:
| v=DMARC1; p=quarantine; rua=mailto:example@domain.com; ruf=mailto:email@domain.com; fo=s |
Where:
- v — A mandatory tag-value (don’t change it!).
- p — Mail processing policy. One of the possible options is specified — none, quarantine, or reject.
- rua – Email address for receiving statistical reports. The address must belong to the same domain for which the DMARC record is configured.
- ruf — Email address for receiving reports on failed authentication checks. Since each error when verifying the sender’s address generates a separate report, it’s better to have a separate mailbox for this.
- fo — Determines in what cases reports will be sent to the domain owner. Possible values include:
- 0 — a report is sent if SPF and DKIM checks fail. Set by default.
- 1 — a report is sent if one of the checks fails — either SPF or DKIM.
- d — a report is sent for each DKIM verification performed.
- s — a report is sent for every SPF check performed.
I have set up SPF, DKIM, and DMARC, but email deliverability is still low
Even if you’ve set up SPF, DKIM, and DMARC records, your recipients’ inboxes might not completely trust you. That’s often the case when you have a new domain.
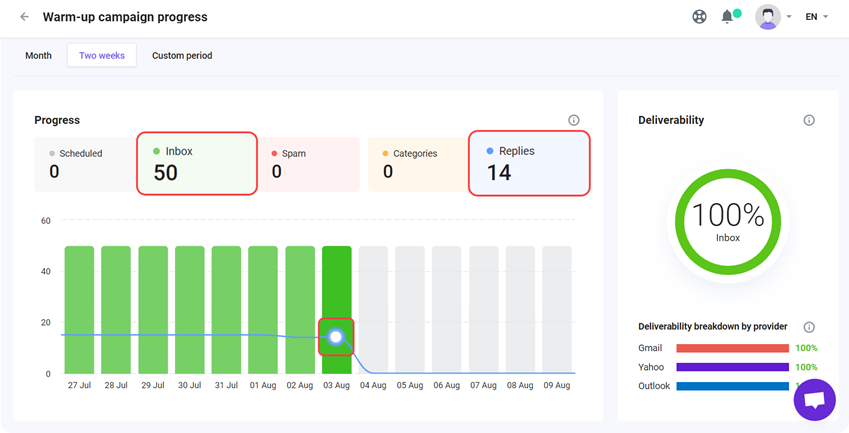
To prove to ESPs that you’re a trustworthy sender, you should warm up your domain before launching bulk email campaigns. Luckily, with Snov.io Email Warm-up, you can do it easily.
We’ve designed this tool to help users increase their email deliverability and improve sender reputation.
The tool’s hyper-intelligent AI will craft realistic same-thread conversations and ensure your emails don’t land in spam. As a result, after the first campaign, you will enjoy open rate growth and higher deliverability.
Wrapping up
Now that your SPF record, DKIM record, and DMARC policy are set correctly, and you’ve warmed up your email account, all that’s left to do is to start sending your cold emails!
And remember, Snov.io Email Drip Campaigns tool is always ready to help you with your email outreach.
Happy sending!